These components can be understood within the Functional Services Framework model. This framework is not specific to any particular type of organization, technology, or use. It is portrayed here in layers (see figure 1), similar to models of network protocols, but is more generally intended as a way to think about the components of a feature-rich, flexible, open, and distributed infrastructure.
FIGURE 1. network Functional Services Framework
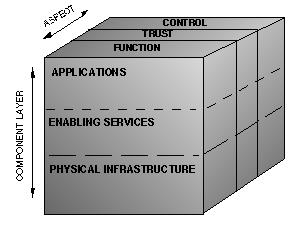
The Functional Services Framework model is used to characterize the network by function and by certain key characteristics (described below); it does not provide any details about these functions. For example, while the general framework might be used to locate supporting software for handling accounting information in an information access service, it would not give any details of expected performance or of a particular implementation, which would be dependent on its capability and design. The detail required for such a particular instance would be described in a domain-specific architecture for a service or application.

